Scientific Posters
Here you can find the scientific posters that were exhibited on the Open House Day
Title: Optimal Source Selection inP2P IPTVBased on Abandon Probability
Author: Alex Bikfalvi, Jaime García-Reinoso, Iván Vidal, Francisco Valera
Publication date: 19th November 2010
Abstract: In peer-to-peer (P2P) IPTV, a new client selects one or more source peers that already receive the desired video stream and use their upstream connection to forward the video content. The importance of source selection becomes greater when multiple TV channels are available and the user tendency to browse increases the peer churn and negatively a
ects the overall performance. However, existing solutions focus on peers receiving several streams at the same time (a primary channel that is played-back to the user, and a number of secondary ones to serve the downstream peers) that may be too expensive over a long period, or optimize the peer selection based on users channel switching patterns.
Title: The Tragedy of the Interdomain Routing Commons
Author: Andra Lutu, Marcelo Bagnulo
Publication date: 19th November 2010
Abstract: N/A
Title: Multipath TCP and multipath routing
Author: Iljitsch van Beijnum
Publication date: 19th November 2010
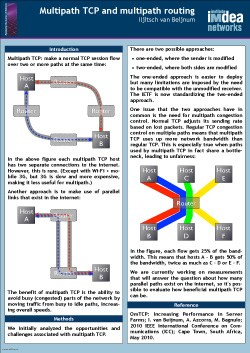
Abstract: Normal TCP/IP operation is for the routing system to select a best path that remains stable for some time, and for TCP to adjust to the properties of this path to optimize throughput. By executing TCP’s congestion control algorithms on multiple paths at the same time, a multipath TCP can shift its traffic to a less congested path, thus maximizing both the throughput for the multipath TCP user and leaving more capacity available for other traffic on more congested paths. And when a path fails, this can be detected and worked around by multipath TCP much more quickly than by waiting for the routing system to repair the failure.
Title: Vehicular Networks: A reality not too far to come
Author: Marco Gramaglia
Publication date: 19th November 2010
Abstract: Intelligent Co-operative Systems that are based on vehicle-to-vehicle (V2V) and Vehicle to Infrastructure (V2I) communications are the next big challenge in automotive electronics and Intelligent Transport Systems.
Title: UNDERSTANDING PIRATE BAY Ways of Measuring BitTorrent
Author: Michal Kryczka, Ruben Cuevas, Arturo Azcorra
Publication date: 19th November 2010
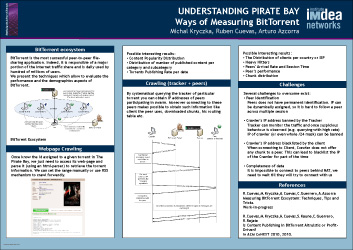
Abstract: BitTorrent is the most successful peer-to-peer file-sharing application. Indeed, it is responsible of a major portion of the Internet traffic share and is daily used by hundred of millions of users.
We present the techniques which allow to evaluate the performance and the demographics aspects of BitTorrent.
We present the techniques which allow to evaluate the performance and the demographics aspects of BitTorrent.
Title: Wireless Mesh Networks as an Alternative to Conventional Wired Backhaul Deployments
Author: Paul Patras
Publication date: 19th November 2010
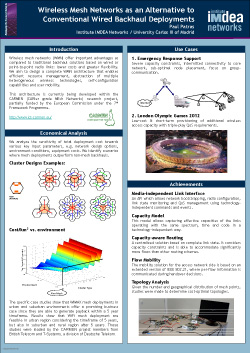
Abstract: Wireless mesh networks (WMN) offer important advantages as compared to traditional backhaul solutions based on wired or point-to-point radio links: lower costs and greater flexibility. We aim to design a complete WMN architecture that enables efficient resource management, abstraction of multiple heterogeneous wireless technologies, self-configuration capabilities and user mobility.
Title: Impact of Prefix Hijacking on Payments of Providers
Author: Pradeep Bangera and Sergey Gorinsky
Publication date: 19th November 2010
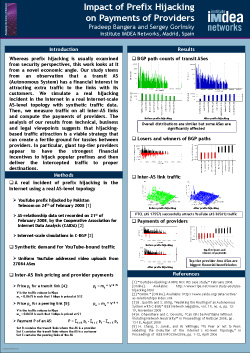
Abstract: Whereas prefix hijacking is usually examined from security perspectives, this work looks at it from a novel economic angle. Our study stems from an observation that a transit AS (Autonomous System) has a financial interest in attracting extra traffic to the links with its customers. We simulate a real hijacking incident in the Internet in a real Internet-scale AS-level topology with synthetic traffic data. Then, we measure traffic on all inter-AS links and compute the payments of providers. The analysis of our results from technical, business and legal viewpoints suggests that hijacking-based traffic attraction is a viable strategy that can create a fertile ground for tussles between providers.